
Nick L is one of the Senior CTI Consultants in the SecAlliance Team. He comes from a diverse background having worked in Law Enforcement and the Financial Services, with a wealth for Investigation, Tactical/Operational CTI, and Incident Management Experience. He was part of an international Cyber Task force in 2017 at the NCFTA in Pittsburgh and has received several commendations for his services to Cybercrime and Investigations. Nick was one of our speakers at the 2025 Cyberhagen Conference, where he spoke about his analysis of Bumblebee Malware.
Over the last couple of nights Nick, has been keeping his investigative tradecraft skills sharp hunting malicious infrastructure in the wild. While a senior CTI Consultant navigating the strategic threat landscape by day, by night Nick likes nothing better than hunting for malicious infrastructure, deepening his tactical insight into current and emerging threats and helping the digital community by sharing knowledge and bolstering awareness and defensive posturing.
Nick started his investigation following the provision of a generic IOC which was time-stamped in the past 48 hours. The IOC appeared to have been automatically collected with no additional CTI context, other than it being a potential threat.
As such, Nick decided to investigate further, seeking to understand the ‘why’ – why it was flagged as malicious – and the ‘what’ – what the entity related to. One of the methods in Nick’s investigative toolbox is TLS foot printing of malicious infrastructure using JA4 in conjunction with other artefacts and behaviours. JA4 was introduced in 2023 by FoxIO, and is a TLS fingerprinting method developed to identify and track TLS handshake behaviour. Often used to enhance network traffic analysis by defenders, it can also be used by CTI professionals to identify infrastructure characteristics and pivot to other artefacts of interest.
Using sandbox technologies, internet scanning and traffic analysis tooling, Nick was able to identify the JA4 TLS signature of the entity (Client Side). This led him towards a vast collection of malicious artefacts. With multiple potential avenues of investigation, Nick decided to focus on further investigation of one data set.
After a few hours, chasing rabbits, pulling threads, plenty of coffee and iterations of the intelligence lifecycle, Nick managed to identify shell scripts, dropped files, Java scripts, further URLs and domains, IP addresses and some detailed procedures, eventually discovering the payloads associated with the entity.

https://www.joesandbox.com/analysis/1803926/0/iochtml
Consolidating the data, Nick ultimately determined that he had likely identified infrastructure and behaviour associated with a new malware strain known as “JSCoreRunner”, which was targeting MACH-O file formats – suggesting the targeting of MAC devices – while obfuscated as a PDF converter with defence evasion capabilities. (below is a Screen Shot from August 2025).
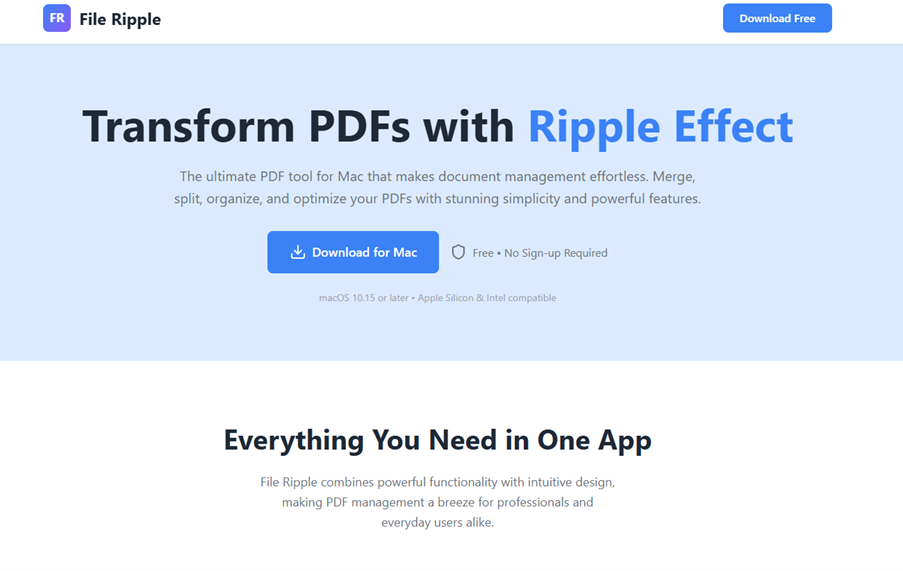
https://web.archive.org/web/20250806211733/https://fileripple.com/
After some further research, it turns out the malware was first reported in late August 2025 by Mosyle, a well-known Mac security researcher.
Rather than being disappointed about an evening wasted uncovering an already-discovered malware, Nick’s investigation demonstrates the utility of pivoting from IOCs and using JA4 signatures to identify, track and understand current threats.
Fuelled by coffee and curiosity, Nick’s research remains ongoing. Findings from this and other research are fed back into our internal teams for broader awareness and use in various products and services for the benefit of current and future clients, including MDR and ThreatMatch reporting.
For more information contact us at info@secalliance.com.