
In the first of this two-part blog series, SecAlliance analysts offer insight into the evolving disinformation threat landscape and how our detection capabilities are helping organisations stay ahead of narrative-based attacks.
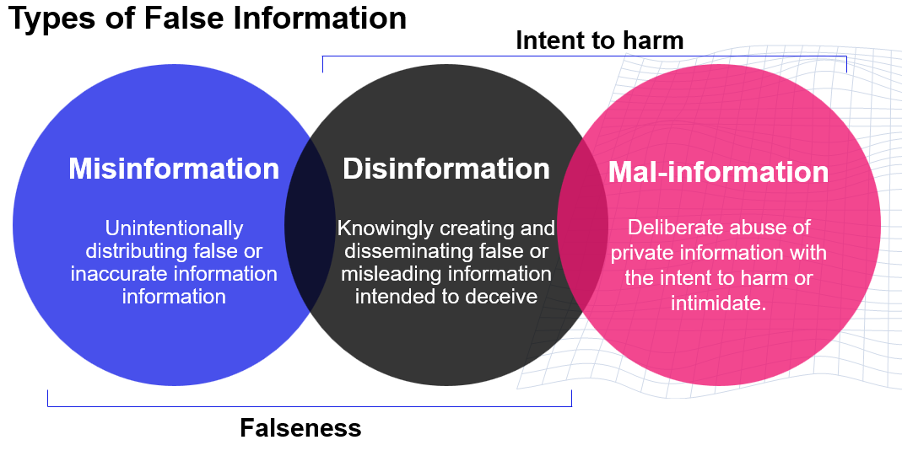
Disinformation is false or manipulated information deliberately created to deceive. Separate from misinformation, which is created or spread unintentionally, disinformation is a targeted tactic often used to erode trust, damage reputations or influence public perception.
In the corporate space, this could look like:
Disinformation is spread by a variety of actors, each with distinct motivations. These include, but are not limited to:
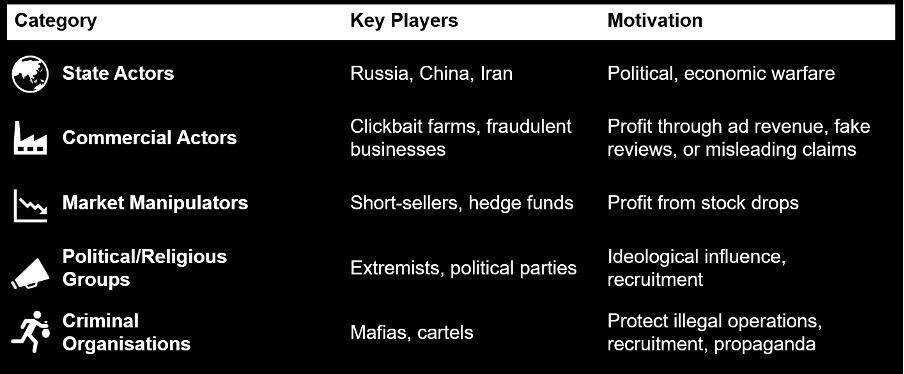
Some of the most coordinated disinformation activity comes from states or state-linked entities, which manipulate information to influence public opinion, sow discord and undermine trust in institutions, or disrupt societies, economies, or political systems in support of wider national and geopolitical objectives. Among the most active and sophisticated actors in this space is Russia. Russia uses disinformation to undermine trust, manipulate decision-making and advance its national interests across multiple fronts. By flooding media spaces with false or misleading information, Russia weakens public confidence in governments and corporate institutions, exploits cultural and political divisions and sows doubt about geopolitical policies that threaten its interests, such as Western sanctions or military aid to Ukraine.
Moscow’s disinformation campaigns are strategically designed to evoke legitimacy and manipulate perception at scale. A common tactic involves cloning trusted Western news sites, such as The Guardian or Le Monde, by duplicating their design and publishing false stories under misleading URLs. Beyond impersonation, entire fake media outlets are created to mimic Western publications. Outlets like The London Crier or DC Weekly serve as vehicles for AI-rewritten news stories or entirely fabricated narratives while appearing independent and legitimate.
Russia’s newer tactics also leverage AI-generated content to create deepfake videos and audio, fake interviews and fabricated news stories.
These operations do not operate in isolation. They are part of interconnected amplification networks that include entities like Pravda.ru, NewsFront, and SouthFront. These platforms regularly recycle and cross-link content to create the illusion of consensus and legitimacy. Amplification also relies on botnets, paid promotion, and coordinated activity across platforms like Telegram, X, and Facebook. Tactics include mass-tagging journalists, flooding comment sections, and manipulating algorithms to boost visibility. The goal is to confuse audiences, distort public discourse, and undermine trust in reliable sources.
While traditionally viewed as targeting political figures, governments or civil society, these operations are increasingly impacting corporations across various industries, including defence, energy, sport, pharmaceuticals, tech, finance and academia. The goal is not just reputational damage – it is to disrupt operations by sowing internal confusion, eroding employee and consumer trust, triggering regulatory or legal scrutiny or inciting public backlash that forces a crisis response. These actions can distort markets, derail partnerships or acquisitions and undermine a company’s competitive advantage by weakening investor confidence.
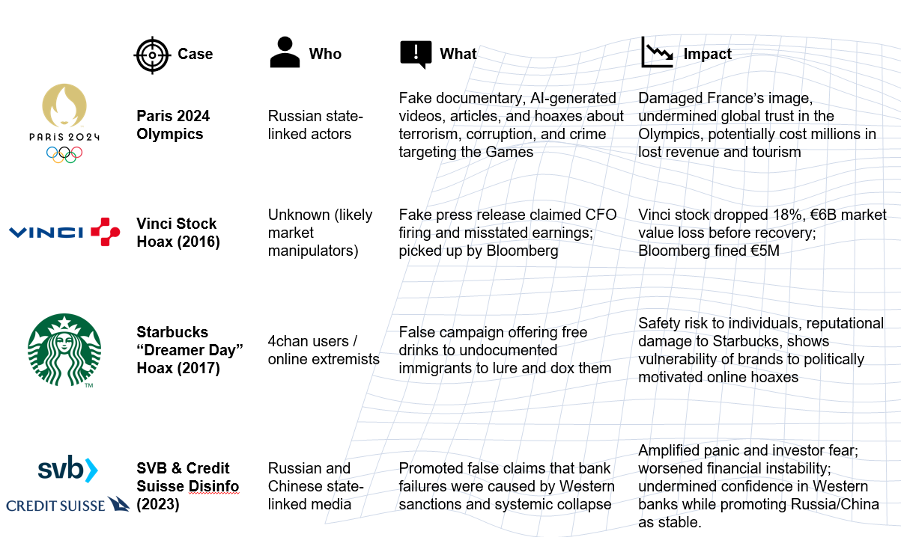
For example, in November 2016, French construction giant VINCI was the target of a coordinated disinformation attack involving multiple fake press releases claiming accounting fraud and the CFO’s resignation. The hoax, distributed via email, led to major news outlets reporting the story, causing VINCI’s stock to plummet by nearly 20% and wiping out approximately EUR7 billion in market value before trading was halted. VINCI denied the claims, confirming there was only impersonation and no security breach. The perpetrators remain unidentified, though one anonymous source hinted at activist motives. The incident prompted a market investigation and in 2019, Bloomberg was fined EUR5m by French regulators for spreading the false report without adequate verification.
In another example, in early 2023, panic surrounding the collapse of Silicon Valley Bank was amplified by a mix of actors including Russian- and Chinese state-linked media. While not centrally coordinated, these actors collectively spread alarm across platforms like Twitter and WhatsApp, accelerating a massive USD40 billion+ deposit exodus in a single day.
There are plenty of other examples where banks have been subject to disinformation and misinformation, from the 2019 Metro bank hoax, to the 2022 BlackRock "owns half of Ukraine" false narrative. The latter has been catalogued by EUvsDisinfo as part of a recurring pro-Kremlin theme portraying global financial elites like BlackRock as orchestrators of Western dominance and elite cabals and Ukraine and Zelenskyy as mere puppets to external forces.
Sporting events such as the Olympics are also not immune to state-sponsored disinformation efforts. In 2024, Russian launched a sophisticated disinformation campaign aimed at undermining the Paris 2024 Olympics. This involved used AI-generated deepfakes—such as a fake Tom Cruise documentary titled “Olympics Has Fallen”—plus fabricated press releases from the CIA warning of terror threats to sow fear and discourage attendance. We will take a deeper dive into this topic in our next SecAlliance blog post.
And it is not just states or market manipulators involved in disinformation efforts, as was seen in the 2017 Starbucks “Dreamers Day” hoax. This viral hoax falsely claimed Starbucks was giving free drinks to undocumented immigrants as a political protest, spreading widely on social media with a fake coupon bearing the Starbucks logo. The company debunked the claim, but the disinformation stirred backlash and was traced to online trolls aiming to inflame anti-immigrant sentiment.
These examples show the impact that disinformation can have on a company’s reputation and operations, as well as on its share price, and that this threat should not be underestimated. In 2024, the World Economic Forum listed misinformation and disinformation as the number one short-term threat to the global economy, while academic research by the University of Baltimore has conservatively estimated the cost of disinformation to the global economy to be more than USD78 billion a year.
At SecAlliance we’ve seen firsthand disinformation used as a weapon:
The consequences are real: reputational damage, market impact, executive risk and loss of trust.
At SecAlliance, we use real-time alerting and AI integrated tracking tools to detect narrative attacks early, so our clients can act before the damage is done.
We actively monitor:
Disinformation is evolving fast. We're here to help you stay ahead of it.
For details on our disinformation detection services, please contact info@secalliance.com.