
Over the past two years, SecAlliance has monitored online sources to collect data on hacktivist activity related to the Russia-Ukraine war. Now, as the war enters its third year, we have looked back at the data collected to assess key trends and apply possible lessons for the future of hacktivism in the conflict.
We observed individuals and groups mainly collaborating on the encrypted messaging platform Telegram. Hacktivists used public and private chats to choose victims to target, to share leaked data, and to boast about attacks—real or fabricated. Throughout this report, we have compiled graphics using data collected from these Telegram channels, including information on the threat actors responsible and the types of attacks that they conduct, and who, where, and when they targeted from 01 January to 31 December 2023.
Overall, SecAlliance observed hacktivist activity rates progressively increase throughout 2023—although much of the activity observed was attributed to one group, NoName057. NoName057 was responsible for most distributed denial-of-service (DDoS) attacks, while pro-Russia, state-linked groups claimed the majority of ‘hack-and-leak’ operations. Other stats to note include the following:
Throughout this report, the statistics provided are based on claimed attacks rather than confirmed successes. This allows us to assess hacktivist intent in the context of the Russia-Ukraine war rather than the targets’ capacities to defend against such attacks. Similarly, we have purposefully excluded data collected from certain threat actors, such as Anonymous Sudan, who cite varying geopolitical motivations for their attacks despite their likely links to Russia.
This does not mean we consider hacktivist intent more significant than attack outcome. The most important takeaway from our collection has been that greater noise from an attacker does not equate to greater effect. Although certain highly active groups have dominated hacktivist news cycles over the past 12 months, there is a danger of overblowing the real impact that hacktivists have on the cyber threat landscape—and ironically giving them more influence than they deserve.
Before the outbreak of the Russia-Ukraine war, hacktivism—a portmanteau of hacking and activism—was generally thought to be on the decline. This changed shortly after the invasion when the Ukrainian government announced the creation of The IT Army of Ukraine, inviting volunteers in Ukraine and around the world to participate in retaliatory cyber attacks against Russian entities (for a more in-depth discussion, see our blog The Changing Landscape of Hacktivism).
Today’s hacktivists have not necessarily increased in sophistication; however, the tools now available allow even the least tech-savvy actors to become involved in hacktivism. This is clear based on the volume of activity; in 2023, SecAlliance recorded over 4,000 named hacktivism targets relating to the Russia-Ukraine conflict, not including the large number of individual doxing attempts carried out by pro-Russian threat actors.

Hacktivists primarily conducted distributed denial-of-service (DDoS) attempts in 2023, with 3,820 incidents recorded—over 90% of total hacktivist activity. DDoS attacks aim to disrupt endpoints or networks, temporarily shutting down webpages or other critical public-facing services. DDoS is a favoured hacktivist technique because of the low technical sophistication generally required—often merely requiring the download of a pre-made DDoS toolkit, such as NoName057’s DDoSia.
Although DDoS activity is high, such attacks are also easily countered by organisations so long as precautionary measures are in place, which reduces their impact. Most hacktivist actors on Telegram claim successful DDoS attacks by including a ‘Check-Host[.]net’ report showing that the victim site is down. However, these reports can be unreliable, as they may show a site as down when geo-fencing, rate-limiting, or other defensive measures against DDoS attacks are responsible for limiting access.
In comparison, only 80 data breaches were recorded in 2023, followed by 52 defacement attacks. Data breaches garner significant accolades from other threat actors and are likely to attract media attention but are generally difficult to carry out against strategically significant targets. It should be noted, however, that groups that carried out successful data breaches were less likely to also carry out DDoS attacks, meaning that their overall activity levels may have been lower, but their impact levels were likely to be higher.
Defacement attempts, where threat actors ‘vandalise’ public-facing webpages to delete content or replace it with ideological or offensive material, harken back to the early days of hacktivism. However, most observed defacement activity was carried out in the earlier stages of the Russia-Ukraine war or by newer or smaller groups seeking to increase their notoriety. Defacement attacks on prominent targets are generally unlikely to be successful, as high-value organisations usually—but not always—have better security measures in place. Measures such as vulnerability management for webpage platforms or plugins, or anti-bot measures, which may also protect from DDoS attacks, help protect from opportunistic defacement attacks.
In very few instances, we also recorded claims of disruptive or destructive hacktivist activity, beyond targeting public-facing webpages. These attacks aimed to disrupt critical services or communication systems, sometimes by deploying wiper malware to destroy victim data. As they require higher degrees of sophistication, they were almost exclusively claimed by Russian state-linked groups, such as the group Solntsepyok, which claimed destructive attacks on Ukrainian military and telecommunications entities in 2023.
Throughout 2023, we observed at least 34 different groups claiming hacktivism-related attacks. Most groups’ activity was sporadic or opportunistic, or conducted in large bursts but inconsistently over time. This likely reflects the fact that hacktivism does not yield direct financial or political gains for participants—unlike other forms of cyber threat activity—meaning that there is less incentive to participate.
For example, Killnet, one of the most active groups early in the conflict, conducted significant targeting of the US healthcare sector at the beginning of the year, only for activity levels to drop significantly in the following months. Part of the declining activity may be attributed to a loss of enthusiasm by members—Killnet’s Telegram channel evolved to predominantly advertise money-making schemes throughout 2023. Likewise, in December 2023, KillMilk, one of its leading organisers, announced their ‘retirement’ from hacktivism and was subsequently allegedly doxed by Russian media, suggesting a breakdown in relations with Russian authorities.
In contrast, People’s Cyber Army, the second-most active group, which also has alleged ties to Russian state-backed groups, conducted consistent attacks against Ukraine, targeting Ukrainian entities every week of 2023. Most of these attacks were DDoS; however, the group also leaked data allegedly obtained from Ukrainian government organisations on multiple occasions. Its targeting of entities outside Ukraine was, however, minimal.

Overall, one group was responsible for the vast majority of total hacktivism claims: NoName057. NoName057—aka NoName057(16)—claimed nearly 2,500 attacks throughout 2023, approximately 60% of all incidents. NoName057 is a pro-Russian hacktivist group, which first emerged in March 2022 and whose operators are largely Russian speaking. Known for its bright, bear-themed imagery, the group almost exclusively conducts DDoS attacks, predominantly in response to geopolitical events. NoName057 consistently named targets every week throughout 2023. At its least active, the group claimed 22 successful attacks, while at its most active, it claimed 78 attacks. Although NoName057 overwhelmingly targeted European entities, most of its targeting was focused on targets outside Ukraine—namely its neighbours and NATO countries.
NoName057’s DDoS efficacy has been linked to its disciplined coordination levels and custom tooling. The group operates the DDoSia project, a subscription-based tool available for NoName057 members and followers. The tool has two versions, one written in Go and one in Python, both consisting of an automatic script able to launch a DDoS attack against a target, ultimately requiring minimal user skill to execute an attack.
During multiple weeks observed by SecAlliance, when more ‘social’ hacktivist groups showed decreased activity rates, NoName057 maintained high activity levels, demonstrating a professionalism not typically associated with hacktivist groups. However, the actual impact of its attacks is diminished by the fact that the group virtually exclusively focuses on DDoS rather than more difficult data breaches and destructive campaigns.
SecAlliance assesses that many pro-Russian hacktivist groups discussed in this report collaborate to some degree with Russian state actors based on third-party reporting and our own analysis. Groups with assessed links to Russian state actors were more likely to conduct data theft or destructive attacks than other groups.
Pro-Russian hacktivist groups’ links with Moscow are commonly acknowledged by both intelligence services and researchers. Ukrainian security services have reportedly previously identified Solntsepyok as a front for the Russian state-backed advanced persistent threat (APT) group Sandworm. Sandworm is itself attributed to Unit 74455 of Russia’s military intelligence services, the Main Intelligence Directorate (GRU). Other researchers have also previously reported on links between hack-and-leak hacktivist groups such as XakNet Team and People’s Cyber Army, and GRU-sponsored APT28.
During our own collection, we observed Solntsepyok claiming multiple data breaches or disruptive attacks that correlated with confirmed attacks attributed to Sandworm. In December 2023, Solntsepyok claimed responsibility on Telegram for the widely reported destructive attack on the Ukrainian telecommunications company Kyivstar. The Security Services of Ukraine (SBU) subsequently attributed the attack to Sandworm.
Not all Solntsepyok claims were, however, verifiable. In August 2023, Solntsepyok claimed to have destroyed ‘the entire strategic electronic intelligence system of the Main Intelligence Directorate of the Ukrainian Defense Ministry’ (HUR) and claimed to have obtained access to Polish, Ukrainian, and British workstations, assisted by HUR employees. We were unable to confirm this claim, but it shortly followed public reporting on Sandworm’s ‘Infamous Chisel’ campaign targeting Ukrainian military devices and Starlink connections. There is a realistic possibility that the claim was made in retribution for the reporting, or as disinformation to distract from the reports.
Solntsepyok has also been observed conducting DDoS attacks. In September 2023, Solntsepyok targeted Estonian government entities in DDoS attacks as part of an alleged joint campaign with the hacktivist groups Beregini, RaHDit, Killnet, Zarya, Joker DPR, Wagner, XakNet Team, NoName057, Black Wolfs, BEAR IT ARMY, Voskhod, People's Cyber Army, Patriot Black Matrix, DEADFOUD, Xecatsha, BEARSPAW, Zulik Group, and Anonymous Russia. Given Solntsepyok’s assessed Russian state ties, there is a realistic possibility that other groups operate with some degree of state influence—although it is highly unlikely that they all have direct state links. While Solntsepyok is likely either a front for Sandworm activity or a direct partnership with members of Sandworm, other groups likely collaborate more loosely with Russian state actors.
Unsurprisingly, especially given the potential degrees of Russian state involvement in hacktivist activity, Ukraine was by far the most targeted country in 2023, making up 18% of incidents. However, this number is arguably lower than would be expected and demonstrates the pan-European—and sometimes global—nature of hacktivism in the Russia-Ukraine war.

*This list excludes targeting by Anonymous Sudan, which often names African and Middle Eastern entities as targets, due to the difficulties in assessing motivations in these instances. The group has cited reasons such as the civil war in Sudan and the Israel-Hamas war as motives for its targeting; however, Anonymous Sudan is also assessed to have ties to Russian threat actors and likely operates in support of Russian geopolitical goals.
European countries (excluding Ukraine) made up the majority of targeted countries due to NoName057’s high rates of targeting countries ‘friendly’ to Ukraine. Poland, which has traditional concerns about Russian encroachment, has played a leading role in strengthening European Union (EU) and international responses to the war in Ukraine despite undergoing leadership changes in 2023. Czechia has also consistently supported Ukraine both with military aid and political support since the onset of the war. In contrast, Hungary, led by EU- and Ukraine-sceptic Viktor Orbán, experienced almost negligible targeting throughout the year.
Outside of Europe, targeting the US and Canada is likely due to the US’s significant material and financial support to Ukraine—although aid delivery is currently on hold due to domestic political tensions. Targeting of Canada is in part likely motivated by Canada’s significant Ukrainian diaspora and tense bilateral relations with Russia, which deteriorated significantly following Russia’s 2014 annexation of Crimea. The Five-Eyes intelligence relationship between the US, UK, Canada, Australia, and New Zealand likely also plays a part in pro-Russian hacktivist targeting choices.
Although we observed overall targeting of Ukraine trending downward over time, it is crucial to note that this does not suggest that the hacktivist threat to Ukrainian entities has decreased. Whereas non-Ukrainian entities are being targeted by hacktivist actors with low capabilities but high levels of motivation and intent to cause disruption, Ukrainian entities are arguably being targeted by hacktivists with higher capabilities and motivation but with the intent to conduct complex attacks that require greater time and effort. The volume of attacks can therefore sometimes distract from the threat that they pose.
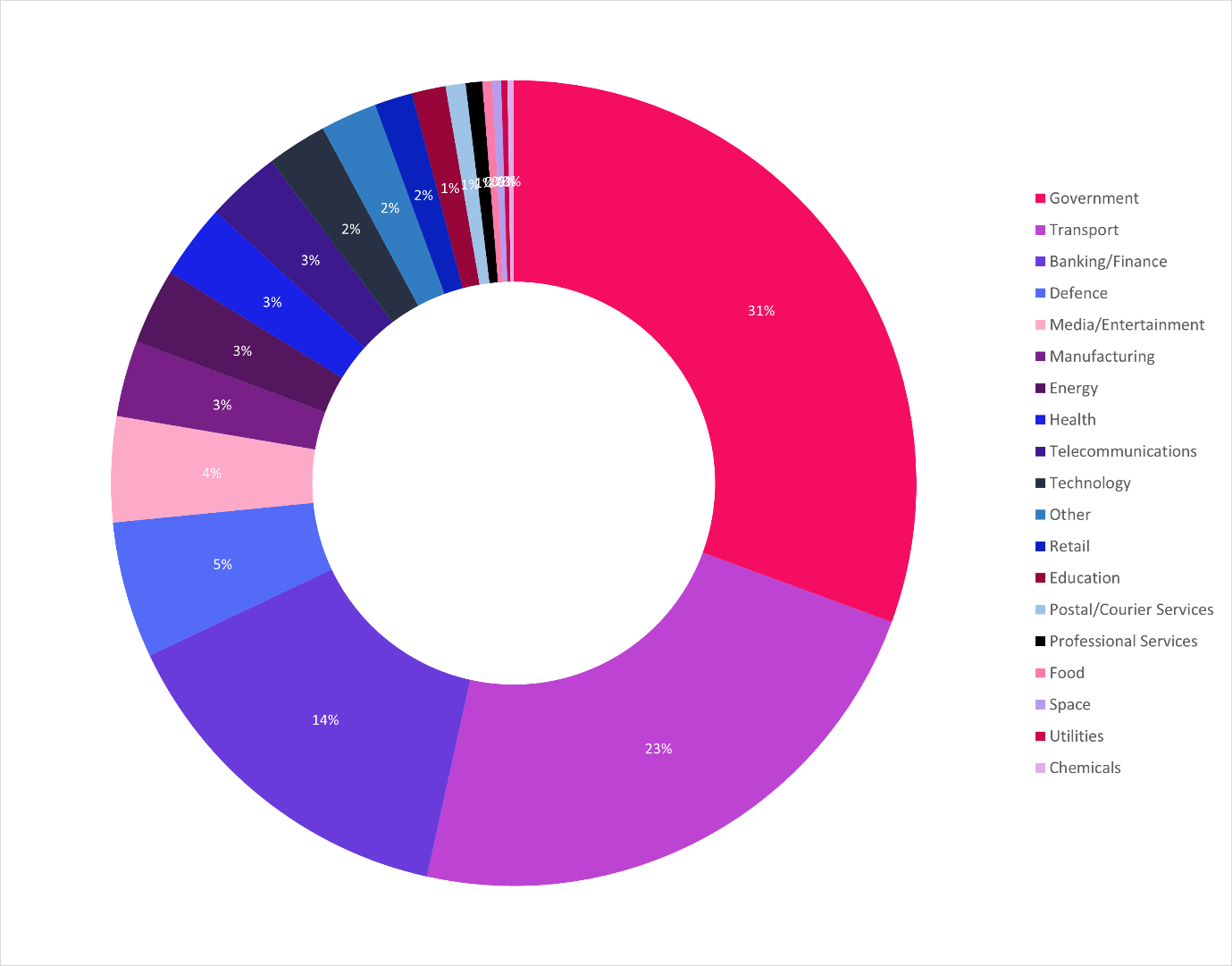
Throughout 2023, we also recorded the sectors of targeted entities. This is particularly important to track for non-governmental entities who may wonder why they are affected by geopolitical developments and when.
In 2023, hacktivism consistently targeted three sectors: government (31% of all incidents), transportation (23%), and financial services (14%). Although a further 18 sectors were targeted—including defence, media and entertainment, healthcare, telecommunications, energy, manufacturing, and technology—government, transportation, and financial services made up more than two-thirds of all recorded targeting attempts.
These sectors were likely targeted due to a combination of notoriety, impact, and ideological motivation. Even minor disruptions of government services are likely to attract significant media attention, while if a government data breach is successful, it also elevates the reputation of a hacktivist group—and may cause legitimate damage to an organisation. Despite protections available for countering DDoS, news agencies repeatedly reported government webpages as impacted by DDoS attacks in 2023. Belgian government webpages temporarily went down in October 2023 following targeting by NoName057. In the same month, Spanish government webpages were unavailable following attacks that corresponded with Spain’s hosting of an EU summit in Granada, while in June 2023 the European Investment Bank site was disrupted by an attack linked to Killnet and Anonymous Sudan.
Transportation and financial services were also likely targeted as they are critical services essential to economies running smoothly. Disruptions of online services, such as ticket-purchasing services, airport webpages, and online banking portals, are also likely to lead to media coverage, as well as brand reputational damages and customer dissatisfaction. In multiple instances in 2023, we observed NoName057 escalating its targeting of financial services explicitly following media reporting on the group’s activities. This also occurred in cases without an external motivating factor, such as a particular geopolitical event.
However, as seen in Figure 1, it is worth noting that not all threat actors targeted the same sectors to the same extent. As previously mentioned, Killnet targeted healthcare services to a much greater extent than any other hacktivist group in 2023. People’s Cyber Army, which predominantly targeted Ukraine, disproportionately targeted media and entertainment entities, plausibly to disrupt pro-Ukraine and anti-Russia messaging. NoName057 targeted transportation entities nearly equally to government organisations—despite predominantly acting in response to geopolitical events—realistically as a means of targeting supply chains and critical services.
Hacktivists conducting data breaches rarely targeted transportation entities, instead focusing over half of all attacks against government and defence entities, followed by financial services, retail, and technology entities to a much lesser extent. Of the data breaches we recorded, over half were conducted against Ukrainian entities.
Throughout 2023, hacktivist groups predominantly cited some form of geopolitical motivation for their activity, either acting in support of the wider Russia-Ukraine war or responding to specific geopolitical events. In a smaller number of cases, groups also cited ideological motivations, including support for labour and other protest movements, religion—particularly Russian Orthodoxy—and anti-fascist motives. The latter reasoning is a common propaganda theme used by Russia to bolster support for the war and reduce international support for Ukraine; however, whether these hacktivist groups were motivated by this narrative or helping deliver it as part of influence operations is unclear.
In a select number of cases, hacktivist groups were also plausibly motivated by internal Russian affairs. Overall activity levels increased moderately immediately following the death of Wagner Group leader Yevgeny Prigozhin, although we are unable to definitively link this to his death. This could realistically have been an attempt to distract from internal Russian divisions, or a celebratory reaction to Prigozhin’s death.
Where hacktivist activity was a reaction to a specific external event, attacks were plausibly emotional and reactive responses rather than rational targeting acts. However, for hacktivist groups with assessed ties to Russian military intelligence, such as Solntsepyok or XakNet, attacks were more likely motivated to support specific Russian political or military goals. In multiple instances, we observed hack-and-leak actors leaking data from organisations that had either previously been or would later be confirmed as having been compromised by Russian state-nexus actors, suggesting that the ostensibly ‘hacktivist’ activity was likely a front for strategically motivated activity rather than ideologically or reactively motivated.
Moscow likely sees Telegram-based hacktivist groups as a tool for coordinating attacks and obfuscating activity by widening the pool of involved actors. DDoS attacks, infrequently used by more sophisticated state-linked actors, are one method to disguise actor attribution and capabilities, as demonstrated by Solntsepyok.
Collaborating with hacktivist groups also likely allows Russia to:
Outsourcing activity to hacktivist groups, especially attacks that require low levels of sophistication, frees up resources for state actors and allows them to maintain plausible deniability when conducting attacks. This is especially important for targeting entities outside Ukraine, which Russia may not wish to antagonise directly.
Conversely, using Telegram channels allows Russia to project its successful cyberattacks to a wider audience and allows state-linked groups to publicise successes. Telegram reportedly has over 800 million users and is a commonly used platform both within and outside Russia. Although many pro-Russian hacktivist groups operate in Russian, some operate in English—NoName057 also specifically maintains an English-language Telegram channel. Since APT groups generally attempt to maintain stealth and persistence in victim environments and do not usually publish attacks, while victims do not necessarily publicly disclose disruptive or destructive attacks, hacktivist groups are a means of skirting these restrictions. As Russia has repeatedly demonstrated the value it places on influence operations, hacktivist groups are likely a valuable tool for publicising attacks and influencing perceptions of the conflict.
In some instances, pro-Russian threat actors also realistically conducted activity in response to pro-Ukrainian hacktivist or state-linked activity. Toward the end of 2023, Ukrainian intelligence agencies and cyber entities claimed multiple disruptive or destructive attacks on Russian entities, which may have motivated Russian actors to respond with similar campaigns.
The social element of hacktivist activity in the Russia-Ukraine war also cannot be overlooked. Most hacktivist channels are quite social, hosting lengthy discussions in their comment streams and allowing members to vote on which countries to target. This likely gives participants the sense that they are actively making a difference in a conflict, as well as feelings of community and inclusion, which are important for building group bonds and encouraging illegal and anti-social behaviour. Small victories, such as successful DDoS attacks, also may give participants the sense that Russia is winning the war, which motivates ideological support for the conflict. However, for certain groups, such as Killnet, individual personalities also likely influenced targeting decisions more so than specific geopolitical events.
Additionally, the fact that this activity is conducted virtually, rather than physically, likely encourages more widespread participation by individuals unlikely to get involved in other cyber threat activity. Participants are more likely to feel protected from prosecution or other legal backlash. Hacktivism also opens participation to individuals worldwide, many of whom will bring their own ideological goals to the conflict, which stem beyond Russia-Ukraine relations. Certain threat groups, such as NoName057, also ‘gamify’ participation in attacks, advertising rankings and even monetary prizes to encourage contributions to DDoS campaigns.
However, it is important to recognise that, while actors may have provided a specific motivation for hacktivist campaigns, like most cyber threat activity, hacktivism remained largely opportunistic in 2023. Although target countries and/or sectors are likely pre-determined, hacktivists generally cast a wide net when conducting attacks, only publicly claiming those deemed successful, such as is the case with NoName057.
Each hacktivist group is likely to have individual motivations and targeting patterns. However, some—like NoName057—offer case studies to assess correlations between specific events and rates of actor activity. NoName057 is particularly suitable for evaluating group motivations, as they helpfully state to which event or development they are responding when conducting attacks.
In 2023, these were largely political developments outside of Ukraine and Russia, such as a third country hosting a multinational summit, a foreign minister proclaiming support for Ukraine, or an announcement of arms being shipped to Kyiv by another country. Generally, NoName057’s targeting was not instigated by battlefield developments; however, this was not true for all hacktivist groups. Some, including those uncoincidentally tied to the GRU, responded more often to military developments than political ongoings.
Below, we have supplied a breakdown of major geopolitical developments, as well as developments cited by NoName057 as reasons for targeting to view correlations:


As seen, certain major geopolitical events triggered little to no response from NoName057. Finland’s accession to NATO resulted in a surprisingly minor increase in the targeting of Finnish entities. In contrast, a meeting of EU foreign affairs ministers held in Ukraine resulted in a significant spike in Finnish targeting after Finland’s foreign minister expressed Helsinki’s support for Ukraine and condemned Russian violations of international law.
Targeting of Poland, which was consistently high throughout 2023, did not see a noticeable increase following the Polish parliamentary elections, even though pro-EU Donald Tusk later formed the Polish government. In contrast, a visit by Poland’s President Duda to Vienna and Poland’s seizure of a Russian embassy school triggered notably increased targeting of Polish entities.
In many cases, as noted by the bracketed dates in Table 1, events that reportedly motivated NoName057 activity did not always result in immediate activity by the group. Poland’s seizure of the Russian embassy school was only cited as a reason nearly two weeks after the event occurred, realistically because it was a minor event that took longer to enter the news cycle. The delay between an event occurring and being cited as a reason for an attack could also plausibly be attributed to the time needed to coordinate and consult with group members and successfully DDoS an entity.
The greatest takeaway from this is that keeping up to date on geopolitical affairs is an important means of staying aware of potential targeting—but unfortunately, there is not always a clear correlation between an event and an attack. Having proper mitigations in place and a strong security posture capable of proactively protecting against DDoS attacks are the best ways to protect from all types of hacktivist activity, even for organisations that do not operate in geopolitically significant sectors.
Hacktivism will likely remain relevant to the Russia-Ukraine war in 2024. Barely two months into the year, we have recorded nearly 1,000 claimed hacktivist attacks—a quarter of those recorded throughout 2023. SecAlliance customers have access to daily, weekly, and monthly reporting on this activity, as well as on other major developments in the Russia-Ukraine war.
The lessons we have extracted from hacktivist activity in 2023 will likely remain the same in the coming year. While DDoS will likely continue to make up the greatest proportion of hacktivist activity, the threat to enterprises will continue to be low, so long as proper mitigation measures are in place. Organisations are recommended to proactively implement DDoS protections and to keep abreast of potentially pertinent geopolitical developments. Relevant events could include the EU parliamentary elections, the Russian and US presidential elections, and developments surrounding international funding for Ukraine, as all of these are also likely to be targeted by Russian influence operations and other cyberattacks.
Hack-and-leak and disruptive operations will most often be conducted against Ukrainian entities, specifically government, defence, finance, telecommunications, and other critical infrastructure organisations. Enterprises outside of Ukraine are almost exclusively likely to be targeted by DDoS attacks—however, some government and financial institutions and critical infrastructure providers in countries friendly to Ukraine face risks of hack-and-leak operations.
Without major changes to the threat actor landscape, NoName057 looks set to continue to be the most prolific threat actor—and we have recently noted increased collaboration between NoName057 and other hacktivist groups and a corresponding increase in hacktivist activity. However, how long this collaboration lasts and whether these attacks have a legitimate impact on targets remain to be seen. State-backed and state-linked hacktivist actors demonstrated the greatest technical sophistication and corresponding impact in 2023, a trend which will most likely continue in 2024.
Military developments in the Russia-Ukraine war will realistically have the greatest impact on the hacktivist threat landscape. Although we did not observe any major evolutions in hacktivist activity throughout 2023, the war was also relatively stagnant throughout this period, despite Ukraine’s major counteroffensive push. So far in 2024, Russian kinetic activity has picked up pace in response to Ukraine’s resourcing and ammunition challenges, taking the city of Avdiivka—the first Ukrainian city Russia has captured in over nine months. If the military status quo changes significantly in the coming year, there is a realistic possibility that the hacktivist threat landscape will evolve. Changes could include focusing more on disruptive or destructive attacks or continuing to undermine international funding for Ukraine.
Recent developments in the cybercriminal threat landscape may also plausibly impact hacktivism in 2024. Following the LockBit takedown, Russian ransomware actors and former LockBit affiliates may turn to more ‘patriotic’ cyber activity, either hacktivism or otherwise supporting Russian state-linked actors. We observed this trend with Conti affiliates following the Conti leaks and self-imposed shutdown, where former affiliates plausibly collaborated with Russian state actors in campaigns targeting Ukraine—although whether they were driven by patriotic duty or as a self-protection means was undetermined.
Whatever developments occur in 2024, the most important takeaway that we observed in 2023 is that, while hacktivism is noisy and attention-grabbing, the actual impact should not be overblown. State actors remain the predominant threat to government and critical infrastructure entities, while cybercriminals pose the greatest threat to enterprises worldwide. Hacktivism should be treated with caution but not given more influence than it merits.